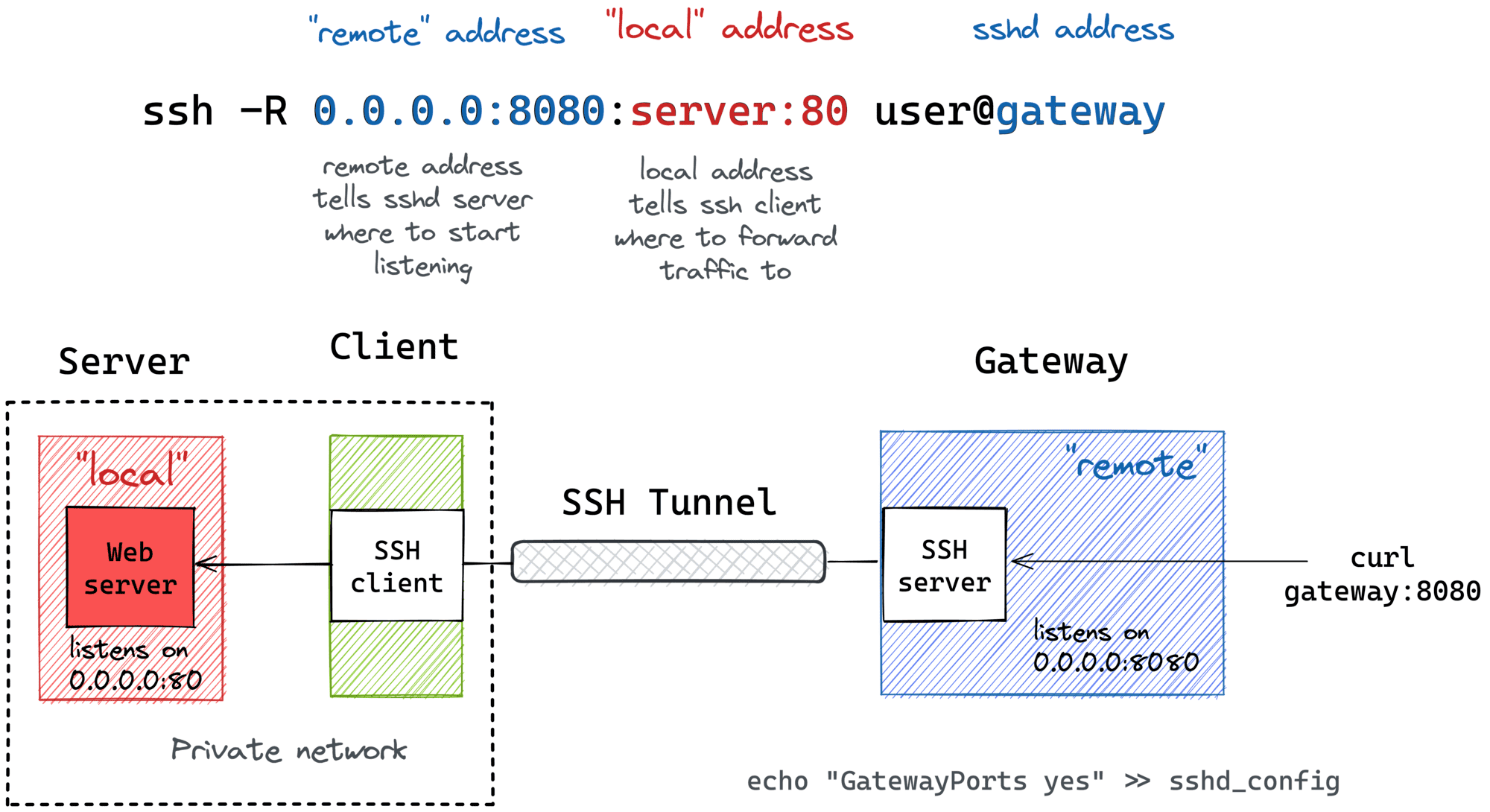
Have you ever wondered how IoT devices securely communicate with remote servers? SSH RemoteIoT Example is your ultimate guide to understanding secure communication protocols in the world of connected devices. Imagine a scenario where your smart home system talks to a remote server without worrying about hackers intercepting your data. Sounds cool, right? Let’s dive into this exciting topic and explore how SSH makes IoT communication seamless and secure.
If you’re new to the concept of SSH RemoteIoT, don’t worry. We’ll break it down step by step so even if you’re not a tech guru, you’ll leave this article with a solid understanding of how SSH works in IoT environments. Whether you’re building a smart home system or managing industrial IoT devices, this guide has got you covered.
SSH RemoteIoT isn’t just about securing data; it’s about creating a reliable infrastructure that ensures your devices operate smoothly without compromising on security. So, buckle up and let’s explore the world of IoT security through the lens of SSH protocols.
Read also:Tom Brady Celebrates Valentines Day With Heartfelt Tribute To Gisele Buumlndchen
What is SSH and Why is it Important for IoT?
SSH, or Secure Shell, is like the superhero of network protocols. It’s designed to provide a secure way for devices to communicate over unsecured networks. In the context of IoT, SSH RemoteIoT Example becomes crucial because IoT devices often rely on remote connections to function properly. Without SSH, your smart fridge could be chatting with a hacker instead of your grocery app. Yikes!
Here’s why SSH matters:
- It encrypts data to prevent unauthorized access.
- It authenticates devices to ensure only trusted systems can connect.
- It provides a secure tunnel for communication, even on public networks.
Think about it this way: SSH is like a private conversation in a crowded room. Only the people involved in the conversation can understand what’s being said. In the IoT world, this means your devices can talk to each other without worrying about eavesdroppers.
SSH RemoteIoT Example: A Practical Overview
Let’s get into the nitty-gritty of SSH RemoteIoT Example. Imagine you have a weather station that collects data and sends it to a remote server for analysis. Without SSH, anyone with the right skills could intercept that data and use it for nefarious purposes. But with SSH, the data is encrypted and securely transmitted, making it nearly impossible for hackers to access.
Here’s a simple example:
Suppose you’re setting up an IoT device to connect to a remote server using SSH. You’d first need to configure the device with the server’s public key. Then, when the device tries to connect, it uses the key to establish a secure connection. This process ensures that only authorized devices can communicate with the server.
Read also:Selena Gomezs Fashion Game Is Stronger Than Evermdashheres Where To Get Her Cozy Puffer Coat
How Does SSH Work in IoT?
SSH operates on a client-server model. The IoT device acts as the client, and the remote server acts as, well, the server. Here’s how the process works:
- The client sends a request to the server to establish a connection.
- The server responds with its public key.
- The client verifies the key and establishes a secure tunnel.
- Data is then transmitted securely between the client and server.
This entire process happens in the background, ensuring that your IoT devices can communicate without any hiccups. It’s like having a personal bodyguard for your data.
Benefits of Using SSH for IoT Devices
Why should you bother with SSH RemoteIoT Example? Here are some compelling reasons:
- Security: SSH encrypts all data, making it nearly impossible for hackers to intercept or modify.
- Authentication: SSH ensures that only authorized devices can connect to your network.
- Reliability: SSH provides a stable connection, even over long distances or unstable networks.
- Scalability: SSH can handle multiple devices and connections without compromising performance.
For businesses and individuals alike, these benefits make SSH an essential tool for managing IoT devices. Whether you’re running a smart home or an entire smart city, SSH ensures that your devices remain secure and functional.
SSH vs Other Protocols: Why Choose SSH?
You might be wondering why SSH is the go-to protocol for IoT devices. Well, let’s compare it to some other popular options:
Compared to HTTP, SSH offers superior security and authentication. While HTTP is great for web browsing, it’s not designed for the secure communication needs of IoT devices. On the other hand, SSL/TLS is another secure protocol, but it can be resource-intensive for smaller IoT devices. SSH strikes the perfect balance between security and efficiency.
Setting Up SSH for IoT Devices
Ready to set up SSH for your IoT devices? Here’s a step-by-step guide:
- Install an SSH client on your IoT device. Many modern devices come with SSH pre-installed, but if not, you can download it from the manufacturer’s website.
- Generate a public and private key pair. This is like creating a unique ID for your device.
- Upload the public key to your remote server. This allows the server to recognize your device.
- Test the connection by establishing a secure tunnel between your device and the server.
It’s important to note that while SSH is secure, it’s not foolproof. Always keep your keys safe and update your software regularly to protect against vulnerabilities.
Common Mistakes to Avoid When Using SSH
Even the best tools can fail if not used correctly. Here are some common mistakes to avoid when setting up SSH for IoT devices:
- Using weak passwords or default credentials.
- Not updating your SSH client and server software regularly.
- Sharing private keys with unauthorized users.
By avoiding these pitfalls, you can ensure that your SSH RemoteIoT setup remains secure and reliable.
Real-World Examples of SSH in IoT
Let’s take a look at some real-world examples of how SSH is used in IoT:
In the healthcare industry, SSH is used to secure communication between medical devices and servers. For instance, a wearable device that monitors a patient’s heart rate can use SSH to send data to a remote server for analysis. This ensures that sensitive health information remains private and secure.
Another example is in the automotive industry, where SSH is used to secure communication between self-driving cars and remote servers. These cars rely on real-time data to navigate safely, and SSH ensures that this data is transmitted securely and without interruption.
Case Study: Smart Home Security
Imagine a smart home system that uses SSH to secure communication between devices. The system includes a smart lock, a security camera, and a thermostat. All these devices communicate with a central server using SSH, ensuring that your home remains secure and your personal information remains private.
This setup not only enhances security but also improves convenience. You can control all your devices from a single app, knowing that your data is protected by SSH encryption.
Best Practices for SSH RemoteIoT
To get the most out of SSH RemoteIoT Example, follow these best practices:
- Always use strong, unique passwords for your SSH keys.
- Regularly update your SSH client and server software to patch vulnerabilities.
- Limit access to your SSH keys and only share them with trusted users.
- Monitor your SSH connections for suspicious activity and take action if needed.
By following these guidelines, you can ensure that your SSH setup remains secure and effective.
Troubleshooting SSH Issues
Even with the best practices in place, issues can arise. Here are some common SSH problems and how to fix them:
- Connection Refused: Check that your server is running and that the correct port is open.
- Authentication Failed: Verify that your public key is correctly uploaded to the server.
- Timeout Errors: Ensure that your network connection is stable and that there are no firewalls blocking the connection.
By addressing these issues promptly, you can keep your SSH RemoteIoT setup running smoothly.
Future of SSH in IoT
As the IoT landscape continues to evolve, so does the role of SSH. With more devices connecting to the internet every day, the need for secure communication protocols has never been greater. SSH is poised to play a crucial role in this evolution, providing a secure and reliable way for devices to communicate.
Looking ahead, we can expect to see advancements in SSH technology, such as improved encryption algorithms and better integration with emerging IoT standards. These developments will further enhance the security and functionality of SSH in IoT environments.
Staying Ahead of the Curve
To stay ahead in the world of IoT security, it’s important to keep up with the latest trends and technologies. Follow industry blogs, attend conferences, and participate in online forums to stay informed about the latest developments in SSH and IoT security.
Conclusion
SSH RemoteIoT Example is your key to securing communication in the world of IoT. By understanding how SSH works and implementing best practices, you can ensure that your devices remain secure and functional. Whether you’re building a smart home system or managing industrial IoT devices, SSH provides the security and reliability you need to succeed.
So, what are you waiting for? Start exploring SSH today and take your IoT security to the next level. And don’t forget to share this article with your friends and colleagues. Together, we can make the IoT world a safer place!
Table of Contents
- What is SSH and Why is it Important for IoT?
- SSH RemoteIoT Example: A Practical Overview
- How Does SSH Work in IoT?
- Benefits of Using SSH for IoT Devices
- SSH vs Other Protocols: Why Choose SSH?
- Setting Up SSH for IoT Devices
- Common Mistakes to Avoid When Using SSH
- Real-World Examples of SSH in IoT
- Best Practices for SSH RemoteIoT
- Troubleshooting SSH Issues
- Future of SSH in IoT