Hey there, tech-savvy friend! If you've ever wondered how to set up a secure connection for your RemoteIoT devices using SSH on AWS, you're in the right place. In this article, we'll dive deep into the world of remote IoT management, focusing on SSH and AWS as the ultimate power couple for your tech stack. Whether you're a beginner or a seasoned pro, this guide will walk you through everything you need to know about remoteiot ssh aws example. So, buckle up and let's get started!
Picture this: you're managing a fleet of IoT devices scattered across the globe. You need a secure, reliable way to connect to these devices remotely without compromising on security. That's where SSH and AWS come in. Together, they create a seamless environment for managing your IoT infrastructure, ensuring your data remains safe and your operations run smoothly.
In today's fast-paced digital world, the importance of secure remote connections cannot be overstated. With cyber threats on the rise, having a robust system in place is not just a luxury—it's a necessity. This article will break down the complexities of remoteiot ssh aws example, making it easy for you to implement in your own projects. Let's make tech work for you!
Read also:Eugene Levy And Catherine Ohara The Untold Story Of Their Friendship
What is RemoteIoT and Why Does It Matter?
RemoteIoT refers to the practice of managing and monitoring Internet of Things (IoT) devices from a distance. These devices can range from smart home gadgets to industrial sensors, all of which require constant attention and maintenance. The ability to control these devices remotely is crucial for efficiency and scalability.
But why does RemoteIoT matter? Well, it allows businesses and individuals to:
- Reduce operational costs by eliminating the need for on-site visits.
- Improve response times to issues, ensuring minimal downtime.
- Scale operations effortlessly as the number of devices grows.
When combined with SSH and AWS, RemoteIoT becomes a powerhouse solution for modern tech challenges. Let's explore how these tools work together to create a secure and efficient system.
Understanding SSH: The Backbone of Secure Connections
SSH, or Secure Shell, is a cryptographic network protocol that enables secure communication between devices over an unsecured network. It's like having a secret tunnel that only you and your devices can access. SSH provides authentication and encryption, ensuring that your data remains private and protected from prying eyes.
Key Features of SSH
Here are some of the standout features of SSH:
- Encryption: SSH encrypts all data transmitted between devices, making it nearly impossible for hackers to intercept.
- Authentication: SSH uses public-key cryptography to verify the identity of devices, ensuring only authorized users can access your system.
- Portability: SSH works across multiple platforms, making it a versatile choice for any tech stack.
By leveraging SSH, you can create a secure environment for managing your RemoteIoT devices. But how does AWS fit into the picture? Let's find out!
Read also:Donny Osmond Joins The Masked Singer Uk Exciting New Chapter For The Legendary Entertainer
AWS: The Cloud Platform Revolutionizing IoT Management
Amazon Web Services (AWS) is the leading cloud platform for businesses and developers worldwide. It offers a wide range of services, including compute, storage, and database management, all of which can be tailored to meet the needs of IoT projects. AWS provides the scalability and reliability required for managing large-scale IoT deployments.
Why Choose AWS for RemoteIoT?
AWS offers several advantages for RemoteIoT projects:
- Scalability: AWS can handle millions of devices without breaking a sweat, ensuring your system grows with your business.
- Security: With built-in security features, AWS keeps your data safe from cyber threats.
- Cost-Effectiveness: AWS operates on a pay-as-you-go model, allowing you to optimize your spending based on actual usage.
When paired with SSH, AWS becomes an unstoppable force for managing RemoteIoT devices. Let's take a closer look at how these two technologies work together.
RemoteIoT SSH AWS Example: A Step-by-Step Guide
Now that we've covered the basics, let's dive into a practical example of setting up a remoteiot ssh aws environment. This step-by-step guide will walk you through the process, ensuring you have everything you need to get started.
Step 1: Setting Up Your AWS Account
First things first, you'll need to create an AWS account if you haven't already. Once you're logged in, navigate to the EC2 dashboard, where you'll set up your virtual server.
Step 2: Launching an EC2 Instance
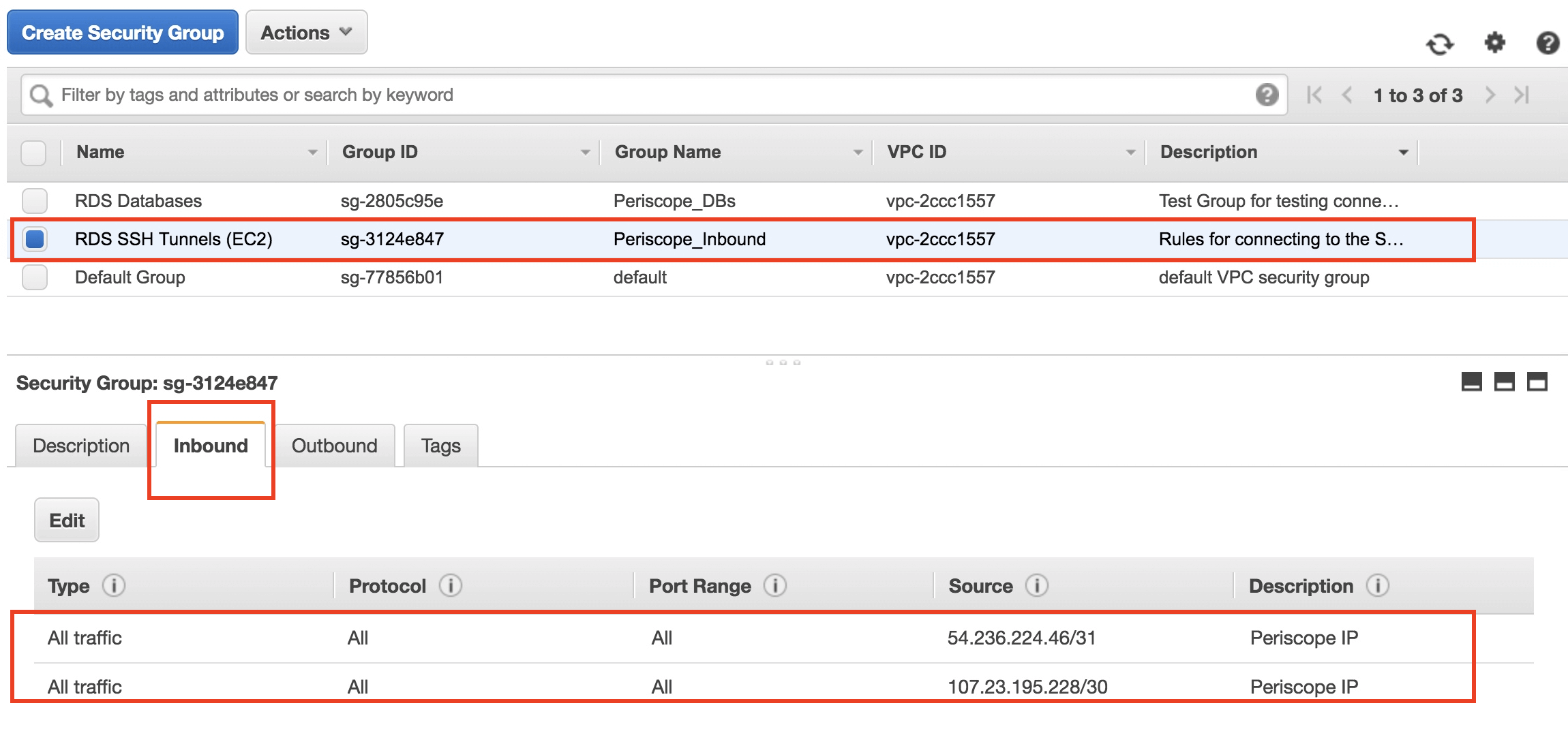
Choose an Amazon Machine Image (AMI) that suits your needs and launch an EC2 instance. Make sure to configure the security group settings to allow SSH access.
Step 3: Generating SSH Keys
Create a new key pair in the EC2 dashboard and download the private key file. This file will be used to authenticate your SSH connection.
Step 4: Connecting via SSH
Open your terminal or command prompt and use the following command to connect to your EC2 instance:
ssh -i "your-key.pem" ec2-user@your-ec2-ip
Replace "your-key.pem" with the path to your private key file and "your-ec2-ip" with the public IP address of your EC2 instance.
Best Practices for RemoteIoT SSH AWS Management
While setting up a remoteiot ssh aws environment is relatively straightforward, there are some best practices you should follow to ensure maximum security and efficiency.
- Use Strong Passwords: Always use strong, unique passwords for your SSH keys and AWS account.
- Regularly Update Software: Keep your operating systems and applications up to date to protect against vulnerabilities.
- Monitor Activity: Regularly check logs and monitor activity to detect any suspicious behavior.
By adhering to these best practices, you can create a robust system that stands up to the toughest challenges.
Common Challenges and How to Overcome Them
Managing RemoteIoT devices using SSH and AWS isn't without its challenges. Here are some common issues and how to tackle them:
Challenge 1: Security Threats
Solution: Implement multi-factor authentication and regularly review access permissions to minimize the risk of unauthorized access.
Challenge 2: Scalability Issues
Solution: Use AWS's auto-scaling features to dynamically adjust resources based on demand.
Challenge 3: Connectivity Problems
Solution: Set up redundant connections and use load balancers to ensure uninterrupted service.
By addressing these challenges head-on, you can create a stable and secure RemoteIoT environment.
Real-World Applications of RemoteIoT SSH AWS
RemoteIoT SSH AWS isn't just a theoretical concept—it's being used in real-world applications across various industries. Here are a few examples:
- Smart Agriculture: Farmers use IoT sensors to monitor soil moisture and weather conditions, managing irrigation systems remotely via SSH and AWS.
- Industrial Automation: Manufacturers leverage IoT devices to monitor production lines, ensuring optimal performance and minimizing downtime.
- Healthcare: Hospitals use IoT devices to track patient vitals, enabling remote monitoring and timely interventions.
These applications demonstrate the versatility and power of RemoteIoT SSH AWS in solving real-world problems.
Future Trends in RemoteIoT SSH AWS
As technology continues to evolve, the future of RemoteIoT SSH AWS looks promising. Some trends to watch out for include:
- Edge Computing: Processing data closer to the source to reduce latency and improve performance.
- Artificial Intelligence: Using AI to analyze data and make predictions, enhancing decision-making capabilities.
- Quantum Computing: Exploring the potential of quantum computing to solve complex problems in IoT management.
These trends will shape the future of RemoteIoT SSH AWS, opening up new possibilities for innovation and growth.
Conclusion: Take Action Today
In conclusion, remoteiot ssh aws example offers a powerful solution for managing IoT devices securely and efficiently. By following the steps outlined in this guide, you can set up a robust system that meets the needs of your projects. Remember to adhere to best practices and stay updated on the latest trends to ensure your system remains cutting-edge.
Now it's your turn! Take action by implementing what you've learned and share your experiences in the comments below. Don't forget to check out our other articles for more insights into the world of tech and IoT. Together, let's build a smarter, safer future!
Table of Contents
- What is RemoteIoT and Why Does It Matter?
- Understanding SSH: The Backbone of Secure Connections
- AWS: The Cloud Platform Revolutionizing IoT Management
- RemoteIoT SSH AWS Example: A Step-by-Step Guide
- Best Practices for RemoteIoT SSH AWS Management
- Common Challenges and How to Overcome Them
- Real-World Applications of RemoteIoT SSH AWS
- Future Trends in RemoteIoT SSH AWS
- Conclusion: Take Action Today